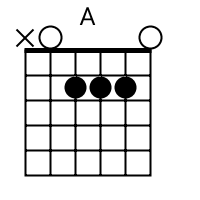
Tab Mapper
The tab mapper is a handy little tool that will render a guitar tab file with graphic chord diagrams displayed alongside. This comes in handy for people who just don't have every single chord shape memorized. Just plug in the web site address of a valid .tab or .crd file and hit "Go". In general, the tab mapper does a better job with printer friendly URLs. If there is more than one way to play a chord, the tab mapper will choose the most common shape. To see other fingerings, click on the chord diagram and you will be taken to the chord calculator.
Original file located @ https://www.keyanalyzer.com/cyber-security/.
Show me scales that sound good with the chords in this song: A.
- Submit a Guest Post (Write For Us)
- About
- Contact us
Keyanalyzer.com
Menu
- Home
- Crypto
- Proxies
- VPN
- Online Services
- Best Software
- WordPress
- AI Technology
Category: Cyber Security
Can Ransomware Infect iCloud? Complete Security Guide for Apple Users
Cyber Security, Cloud Storage, Data Security & Privacy No Comments
Ransomware can potentially affect iCloud-stored files if it encrypts files on your Mac or iOS device that automatically sync to iCloud, but Apple?s built-in security features and architectural design ?
[Continue Reading...]
Is Cloud Storage Safe From Ransomware? A Complete Protection Guide
Cyber Security, Cloud Storage, Data Security & Privacy No Comments
Cloud storage can be vulnerable to ransomware attacks, but proper security measures significantly reduce risks and protect your data from encryption threats. Ransomware is malicious software that encrypts your files ?
[Continue Reading...]
How to Enable Windows 11 Ransomware Protection: Complete Guide to Controlled Folder Access and Security Features
Cyber Security, Data Security & Privacy No Comments
Windows 11 includes built-in ransomware protection through Windows Security that blocks unauthorized applications from modifying your important files. This native protection system uses Controlled Folder Access (CFA) to monitor and ?
[Continue Reading...]
What is a Temporary Email Address? Is It Safe for Verification?
Data Security & Privacy, Cyber Security No Comments
You?re signing up for a website and it asks for your email. You don?t really trust the site. Maybe it looks sketchy or you just don?t want spam filling ?
[Continue Reading...]
Does TikTok Detect VPN Usage? Everything You Need to Know
Tiktok, Cyber Security, Data Security & Privacy, VPN No Comments
TikTok blocks users in certain countries and regions. Maybe you?re traveling overseas and can?t watch your favorite videos. Or perhaps TikTok is banned where you live. You might think ?
[Continue Reading...]
Is OffGamers Legit? Complete Review and Analysis of the Digital Game Store
Cyber Security, Online Services No Comments
OffGamers is a digital game store that has been operating for over 20 years, but many gamers still question whether it?s legitimate and safe to use. The Singapore-based platform ?
[Continue Reading...]
Best Practices for Vulnerability Scanning: A Complete Guide to Network Security Assessment in 2025
Network Security, Cyber Security, Data Security & Privacy No Comments
Vulnerability scanning is a way to find security problems in networks, systems, and applications using automated tools and manual checks. Companies today face more cyber threats, making vulnerability scanning ?
[Continue Reading...]
Best Practices for Vulnerability Management in Cloud Computing: Securing Your Cloud Infrastructure
Network Security, Cyber Security, Data Security & Privacy No Comments
Vulnerability management in cloud computing represents a systematic approach to identifying, evaluating, and addressing security weaknesses within cloud-based systems and infrastructure. The migration of business operations to cloud platforms ?
[Continue Reading...]
How to Identify System Vulnerabilities in Networks: Complete Guide for Cybersecurity Assessment
Cyber Security, Data Security & Privacy, Network Security No Comments
Network vulnerability identification is the systematic process of discovering security weaknesses in computer networks that cybercriminals could exploit. This comprehensive guide will walk you through proven methods to detect ?
[Continue Reading...]
The Complete Guide to 3-2-1 Backup Strategy: Protect Your Data with Proven Methods
Data Security & Privacy, Cloud Storage, Cyber Security No Comments
The 3-2-1 backup strategy is a simple data protection rule that requires keeping three copies of important data on two different storage types with one copy stored offsite. This ?
[Continue Reading...]
- Previous
Search
Recent Posts
- Can Ransomware Infect iCloud? Complete Security Guide for Apple Users
- Is Cloud Storage Safe From Ransomware? A Complete Protection Guide
- What Is Cloud Computing And How Does It Work? A Complete Guide for Beginners and Businesses
- How to Choose the Best Server Location for Your Website: Complete Guide to Geographic Hosting Optimization
- How to Enable Windows 11 Ransomware Protection: Complete Guide to Controlled Folder Access and Security Features
- Cloud Backup vs Cloud Storage: What?s the Difference?
- What is a Temporary Email Address? Is It Safe for Verification?
- Does TikTok Detect VPN Usage? Everything You Need to Know
- 12 Top Cloud Backup Solutions for Small Businesses: Protect Your Data with Enterprise-Grade Security
- What Is an Obfuscated VPN? Your Complete Guide to Bypassing Blocks and Staying Private Online
- 11 Best Invoicing Software for Small Businesses in 2025: Complete Guide with Pricing & Reviews
- Is OffGamers Legit? Complete Review and Analysis of the Digital Game Store
- 15 Free Movie Apps for Android: Your Complete Guide to Legal Streaming in 2025
- Best Practices for Vulnerability Scanning: A Complete Guide to Network Security Assessment in 2025
- Best Practices for Vulnerability Management in Cloud Computing: Securing Your Cloud Infrastructure
- How to Identify System Vulnerabilities in Networks: Complete Guide for Cybersecurity Assessment
- The Complete Guide to 3-2-1 Backup Strategy: Protect Your Data with Proven Methods
- Complete Guide to Ransomware Protection: How to Defend Your Business from Cyber Attacks
- Public Cloud Leakage Prevention: Your Ultimate Guide to Securing Data
Categories
- AI technology
- AI Tools
- Android Apps
- Best Software
- Bitcoin
- Cloud Storage
- Companies
- Computer Security
- Converter
- Crypto
- Cyber Security
- Data Security & Privacy
- Error
- iPhone
- JavaScript
- Leadership
- Movies
- Network Security
- Online Services
- Proxies
- Python
- Risk Management
- ROMs & Emulators
- SaaS
- SEO Tools
- SMS Services
- Social Media Marketing
- Software
- Technology
- Tiktok
- Unblocked Games
- VPN
- Web Development
- Windows
- WordPress
Ads
Keyanalyzer.com Copyright © 2026.
About - Contact us - Privacy Policy - Support & Powered By dataprixa.com
©2026 JGuitar.com