Tab Mapper
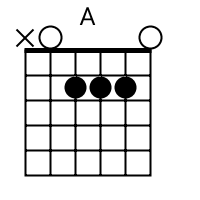
The tab mapper is a handy little tool that will render a guitar tab file with graphic chord diagrams displayed alongside. This comes in handy for people who just don't have every single chord shape memorized. Just plug in the web site address of a valid .tab or .crd file and hit "Go". In general, the tab mapper does a better job with printer friendly URLs. If there is more than one way to play a chord, the tab mapper will choose the most common shape. To see other fingerings, click on the chord diagram and you will be taken to the chord calculator.
Original file located @ http://cisa.gov.
Show me scales that sound good with the chords in this song: A.
An official website of the United States government
Here?s how you know
Official websites use .gov
A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS
A lock ( Lock A locked padlock ) or https:// means you?ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
no-cost Cyber ServicesSecure by design Secure Your BusinessShields UpReport A Cyber Issue
Search
- Topics
TopicsCybersecurity Best PracticesCyber Threats and ResponseCritical Infrastructure Security and ResilienceElection SecurityEmergency CommunicationsIndustrial Control SystemsInformation and Communications Technology Supply Chain SecurityPartnerships and CollaborationPhysical SecurityRisk ManagementHow can we help?GovernmentEducational InstitutionsIndustryState, Local, Tribal, and TerritorialIndividuals and FamiliesSmall and Medium BusinessesFind Help LocallyFaith-Based CommunityExecutivesHigh-Risk Communities
- Spotlight
- Resources & Tools
Resources & ToolsAll Resources & ToolsServicesProgramsResourcesTrainingGroups
- News & Events
News & EventsNewsEventsCybersecurity Alerts & AdvisoriesDirectivesRequest a CISA SpeakerCongressional TestimonyCISA ConferencesCISA Live!
- Careers
CareersBenefits & PerksHireVue Applicant Reasonable Accommodations ProcessHiringResume & Application TipsStudents & Recent GraduatesVeteran and Military Spouses
- About
AboutDivisions & OfficesRegionsLeadershipDoing Business with CISASite LinksCISA GitHubCISA CentralContact UsSubscribeTransparency and AccountabilityPolicies & Plans
no-cost Cyber ServicesSecure by design Secure Your BusinessShields UpReport A Cyber Issue
- Home
Enhanced Vulnerability Management with OpenEoX
By embracing OpenEoX, we as a collective community can proactively eliminate vulnerabilities, safeguard the digital ecosystem at scale, and counter the ever-increasing exploitation speed of threat actors.
CIRCIA Rulemaking Town Hall Meetings
CISA is holding a series of virtual town hall meetings to allow external stakeholders limited additional opportunity to provide input on refining the scope and burden of the CIRCIA Notice of Proposed Rulemaking (NPR) published in the Federal Register
CISA?s 2025 Year in Review
Efficiency. Modernization. Resilience. See how CISA focused tightly on our agency?s core mission: protecting America?s critical infrastructure from cyber and physical threats.
CISA RELEASES GUIDANCE ON BARRIERS TO SECURE OT COMMUNICATION: WHY JOHNNY CAN?T AUTHENTICATE
This guidance outlines key barriers to secure communication and provides actionable recommendations for vendors and asset owners and operators to improve the usability and adoption of secure protocols.
CISA Directive Focuses on Mitigating Risks from End-of-Support Edge Devices
Federal agencies must take immediate action to inventory, remove, and replace all unsupported edge devices. This guidance is relevant for all organizations seeking to strengthen network security and reduce vulnerabilities.
Super Bowl LX: Strengthening Preparation, Building Resilience, Fostering Partnerships
Together with the NFL, DHS, and local, state, and private-sector partners, CISA coordinated a year-long initiative to protect people, venues, and critical infrastructure to ensure a safe and successful championship game.
News Updates
The End is Just the Beginning of Better Security: Enhanced Vulnerability Management with OpenEoX
CISA Announces New Town Halls to Engage with Stakeholders on Cyber Incident Reporting for Critical Infrastructure
CISA?s 2025 Year in Review: Driving Security and Resilience Across Critical Infrastructure
CISA Releases Guide to Help Critical Infrastructure Users Adopt More Secure Communication
Super Bowl LX: Strengthening Preparation, Building Resilience, Fostering Partnerships
Latest Operational Information
CISA Adds One Known Exploited Vulnerability to Catalog
Siemens SINEC NMS
Siemens Desigo CC Product Family and SENTRON Powermanager
Siemens Polarion
Siemens Solid Edge
How can we help?
All AudiencesFind Help Locally
Contact your Region
Assist Visits
Protected Critical Infrastructure Information
Industry
Secure by Design
Information Sharing: A Vital Resource
PCII Program modernized
Joint Cyber Defense Collaborative expands
Small and Medium Businesses
Cyber guidance for small businesses
Supplementing passwords
Doing business with CISA
Educational Institutions
School Safety
Cybersecurity for K-12
K-12 School Security Product Suite
Protecting Our Future: Partnering to Safeguard K-12 Organizations from Cybersecurity Threats
JCDC unifies cyber defenders from organizations worldwide. This team proactively gathers, analyzes, and shares actionable cyber risk information to enable synchronized, holistic cybersecurity planning, cyber defense, and response.
StopRansomware.gov is the U.S. Government's official one-stop location for resources to tackle ransomware more effectively.
SAFECOM works to improve emergency communications interoperability across local, regional, tribal, state, territorial, international borders, and with federal government entities.
Additional CISA Resources
CISA Resources & Tools
CISA offers an array of free resources and tools, such as technical assistance, exercises, cybersecurity assessments, free training, and more.
CISA Events
CISA hosts and participates in events throughout the year to engage stakeholders, seek research partners, and communicate with the public to help protect the homeland.
CISA Services Catalog
A single resource that provides you with access to information on services across CISA?s mission areas.
CISA Training
As part of our continuing mission to reduce cybersecurity and physical security risk, CISA provides a robust offering of cybersecurity and critical infrastructure training opportunities.
- Topics
- Spotlight
- Resources & Tools
- News & Events
- Careers
- About
- X
- YouTube
- RSS
- About CISA
- Budget and Performance
- DHS.gov
- FOIA Requests
- No FEAR Act
- Office of Inspector General
- Privacy Policy
- Subscribe
- The White House
- USA.gov
- Website Feedback